IIoT Solutions
IIoT Solutions
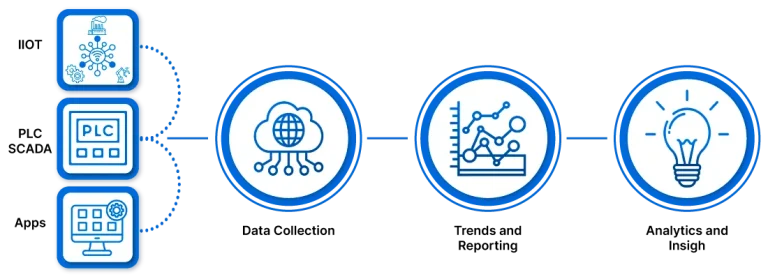
Unlock the Power of Industrial Internet of Things (IIoT) with Prescient Technologies
Services
Key Features
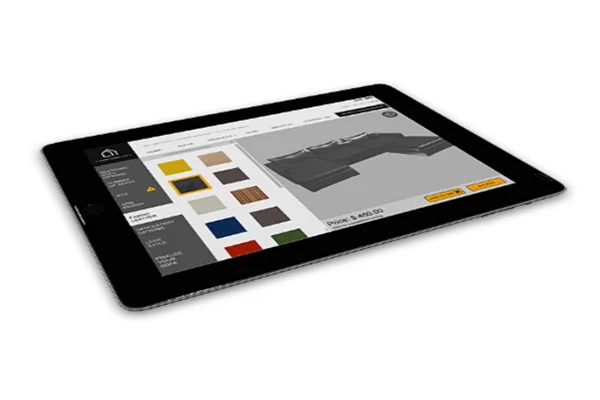
Streamline Operations with Our Management Dashboard
Real-time data visualization and analytics Customizable dashboards for monitoring KPIs Alerting and notification system for proactive decision-making
Material Traceability for transparency and efficiency
End-to-end visibility and tracking of materials Prevention of counterfeit or substandard materials Compliance with regulatory requirements and quality control standards Data-driven insights for optimizing material usage and reducing waste
OEE Monitoring to maximize equipment performance
Real-time monitoring and analysis of equipment performance Calculation and visualization of OEE metrics (availability, performance, quality) Identification of bottlenecks and performance optimization opportunitie Predictive maintenance capabilities to minimize downtime and improve productivity
Energy Management for optimized energy consumption
Monitoring and optimization of energy consumption Identification of energy inefficiencies and savings opportunitie Integration with energy monitoring devices and systems Reporting and analysis of energy usage patterns and trends
Asset Management for effective asset utilization
Remote monitoring and management of industrial assets Condition monitoring and predictive maintenance Asset tracking and inventory management Real-time alerts and notifications for performance deviations
Experience the Power of IIoT
Streamline Operations with Our Management Dashboard
- Real-time data visualization and analytics
- Customizable dashboards for monitoring KPIs
- Integration with industrial systems and sensors
- Alerting and notification system for proactive decision-making
Material Traceability for transparency and efficiency
- End-to-end visibility and tracking of materials
- Prevention of counterfeit or substandard materials
- Compliance with regulatory requirements and quality control standards
- Data-driven insights for optimizing material usage and reducing waste
OEE Monitoring to maximize equipment performance
- Real-time monitoring and analysis of equipment performance
- Calculation and visualization of OEE metrics (availability, performance, quality)
- Identification of bottlenecks and performance optimization opportunities
- Predictive maintenance capabilities to minimize downtime and improve productivity
Energy Management for optimized energy consumption
- Monitoring and optimization of energy consumption
- Identification of energy inefficiencies and savings opportunities
- Integration with energy monitoring devices and systems
- Reporting and analysis of energy usage patterns and trends
Asset Management for effective asset utilization
- Remote monitoring and management of industrial assets
- Condition monitoring and predictive maintenance
- Asset tracking and inventory management
- Real-time alerts and notifications for performance deviations
Why Choose
Prescient Technologies?
-
Expertise in Engineering Process Automation
-
Successful Implementations
-
Seamless Integration and Support
-
Measurable Results

Why Choose Prescient Technologies?
Industry expertise and experience in IIoT implementations
With years of experience, our team possesses deep industry knowledge across various sectors.
Customization and scalability of solutions
Prescient Technologies is at the forefront of technology adoption. We leverage advanced tools such as machine learning and predictive analytics to deliver accurate and actionable insights.
Proactive customer support and maintenance services
At Prescient Technologies, we believe in building long-term partnerships. Our team of dedicated experts is committed to your success at every step. From the initial consultation to ongoing support,
Integration capabilities with existing systems and infrastructure
We recognize that every business is unique. Our solutions are tailored to your specific needs, challenges, and goals.
Robust security measures and compliance
Our success stories speak for themselves. Through our OEE service, we have helped numerous clients achieve significant improvements in productivity, efficiency, and quality.
Our Expertise

Featured Posts
- February 5 2026
- systemadmin
Top Integration Challenges Between MES and PLM – and How to Fix Them
Manufacturing runs on data. PLM manages product definitions. MES controls execution on the shop floor. Problems start when these systems fail to share accurate information. You may see this every day. Engineering updates do not reach production. Shop-floor changes stay isolated. Rework follows. Delays increase. This is why MES and PLM integration challenges remain common across manufacturing organisations. This blog breaks down where integration fails and shows how you can fix it using practical steps and clear examples. MES and PLM Integration Breaks Under Real Conditions PLM and MES evolved for different needs. PLM focuses on design intent and lifecycle data. MES focuses on execution and production tracking. Integration often looks fine on paper but struggles in real use. Common MES PLM integration issues include – When systems fall out of sync, decisions slow down. Errors increase. Teams react instead of planning. This leads many manufacturers to ask:What are the challenges of MES and PLM integration? Why PLM and MES Connectivity Problems Create Rework Integration issues rarely stay isolated. They spread across operations. When PLM and MES connectivity problems exist – Wired has noted that manufacturing data loses value when context is missing between engineering and execution. Even small mismatches can trigger quality issues. Typical outcomes include – This explains why integrating MES with PLM is difficult when alignment is weak. Fix Integration with Structure, Not Shortcuts Effective manufacturing execution system integration with PLM depends on structure and discipline. Successful integration focuses on – Below are the most common challenges, explained with practical fixes and examples. Common Challenges in MES and PLM Integration 1. Data Model Mismatch PLM defines what a product is. MES defines how it is built. These views rarely match by default. Before integration After integration How to fix it This directly explains what causes data issues between MES and PLM. 2. Poor Engineering Change Propagation Engineering changes move fast. MES often lags behind. Before integration After integration Best practices 3. One-Way Data Flow Many integrations only push data from PLM to MES. Feedback never returns. Before integration After integration This closes the loop and answers how to improve MES to PLM data flow. 4. Custom Integrations Without Standards Quick integrations solve short-term needs. They fail during upgrades. Before integration After integration This approach supports long-term stability. 5. Lack of Process Ownership Integration is not only technical. It is organisational. Before integration After integration These steps form the foundation of MES PLM integration best practices. How to Fix MES PLM Integration Problems Step by Step You may ask:How do you fix MES PLM integration problems? Start with clarity, not complexity. A practical approach includes: Phased execution reduces disruption and builds confidence. Best Practices for Sustainable Integration Long-term success depends on consistency. Key MES PLM integration best practices include – These steps reduce rework and improve trust in data. Role of Digital Factory Platforms Digital factory platforms often act as integration layers between PLM and MES. They help: This approach supports consistent execution across plants and regions. Where Prescient Technologies Fits (Balanced View) Prescient Technologies supports manufacturers working through complex MES–PLM integration scenarios. The focus is on: Solutions such as factoryCONNECT, machineCONNECT, and powerCONNECT are examples of platforms that support structured integration and execution control. These tools work best when combined with strong governance and clear process ownership. Key Takeaways Integration succeeds when treated as an operational capability, not a quick technical fix. Final Thought If your teams struggle with MES PLM integration issues, start by simplifying data ownership and change flows. Technology helps, but structure matters more. You can explore platforms such as factoryCONNECT, machineCONNECT, and powerCONNECT as part of a broader integration strategy that aligns engineering and manufacturing with fewer errors and smoother execution.
Read More- January 19 2026
- systemadmin
Best Practices for Integrating MES with PLM and ERP Seamlessly
Manufacturing systems rarely fail because of missing software. They fail because systems do not talk to each other. You may already use MES, PLM, and ERP platforms across your organisation, yet data still moves slowly, manually, or inconsistently. This gap limits visibility and increases operational risk. Seamless integration across these platforms is no longer optional. It is a core requirement for modern manufacturing. This blog explains best practices for integrating MES with PLM and ERP systems, with a clear focus on PLM Implementation, mes software solutions, and digital factory integration. Why MES, PLM, and ERP Integration Matters Each system serves a distinct purpose: When these systems operate in silos, problems emerge quickly. Engineering changes fail to reach the shop floor. Production data does not flow back to design teams. ERP plans rely on outdated execution data. Industry analysis published on TechNewsWorld highlights that manufacturers with integrated MES, PLM, and ERP environments respond faster to design changes and reduce production errors significantly. Integration directly supports cost control, quality, and speed. This is why digital factory integration has become a strategic priority. Understanding the Integration Challenge Integration is not only about connecting software. It involves aligning data models, processes, and ownership. Common challenges include: Without a structured approach, integration efforts create technical debt rather than value. Best Practices for MES, PLM, and ERP Integration The following best practices help you build a stable and scalable integration foundation. 1. Start with a Clear PLM Implementation Strategy Strong integration begins with a solid PLM Implementation. PLM acts as the system of record for product definitions, revisions, and engineering intent. You should ensure that: A weak PLM foundation leads to errors that propagate into MES and ERP systems. Investing time upfront reduces downstream complexity. This approach also supports smoother Teamcenter implementation projects, where data governance plays a critical role. 2. Define System Roles and Responsibilities Clearly Each system must have a clear role. Integration works best when systems share data but do not duplicate ownership. Clear boundaries prevent conflicts and confusion. This clarity is essential when deploying mes software solutions across multiple plants or regions. 3. Align Data Models Across Systems Data inconsistency is a major integration blocker. Part numbers, routings, and process definitions must align across systems. Best practices include: This alignment supports best practices for MES and PLM integration and reduces the need for manual corrections. 4. Use a Layered Integration Architecture Direct point-to-point integrations often become fragile over time. A layered architecture improves flexibility. A typical structure includes: This model supports scalability and simplifies upgrades. It also aligns with modern Application Development Services approaches that focus on modular design. 5. Enable Closed-Loop Feedback from MES to PLM Integration should not be one-directional. Execution data from MES is valuable for engineering teams. When MES feeds data back to PLM: This closed-loop approach strengthens digital factory integration and improves collaboration between engineering and manufacturing. 6. Integrate MES with ERP for Real-Time Visibility Many manufacturers ask how to integrate MES with ERP systems without disrupting operations. The key lies in timing and data relevance. ERP systems need accurate execution data to plan effectively. MES provides: Integration ensures ERP plans reflect reality, not assumptions. This improves inventory accuracy and delivery commitments. 7. Prioritise Data Quality and Validation Integration amplifies both good and bad data. Without validation, errors spread faster. Best practices include: Strong data governance supports reliable mes software solutions and reduces operational risk. 8. Plan for Change Management and Scalability Manufacturing environments evolve. New products, plants, and processes are inevitable. Your integration strategy should support: Scalable design ensures your PLM Implementation and integration efforts remain effective over time. Role of Application Development Services in Integration Off-the-shelf connectors rarely meet complex manufacturing needs. Custom Application Development Services help bridge gaps between systems. These services support: A tailored approach ensures integration aligns with real operational processes rather than forcing process changes to fit software limits. Integration in a Digital Factory Environment In a digital factory, integration is continuous rather than static. Data flows across design, planning, execution, and analytics platforms. Digital factory integration focuses on: Prescient Technologies supports this environment by delivering engineering-focused integration solutions that connect PLM, MES, and ERP systems in a controlled and scalable way. Common Mistakes to Avoid You should avoid: These mistakes reduce long-term value and increase maintenance effort. Key Takeaways Next Steps If you want to integrate MES with PLM and ERP systems without disrupting operations, a structured approach is essential. Clear data ownership, scalable architecture, and strong governance make the difference. Explore how Prescient Technologies’ engineering-led integration capabilities and Application Development Services can help you connect systems while preserving flexibility and control. Connect with our team to discuss a seamless integration strategy for your digital factory.
Read More- January 12 2026
- systemadmin
What is a Smart Energy Management System & How It Reduces Operational Costs
Energy expenses continue to rise across manufacturing facilities. You may already focus on improving production efficiency, reducing downtime, and maintaining quality. Yet energy usage often receives attention only when monthly bills arrive. This lack of visibility quietly increases operational costs and limits control. A smart energy management system helps you close this gap. It brings clarity to how energy flows across your factory and helps you act on real data rather than estimates. This blog explains what is a smart energy management system, why it matters for manufacturing, and how it helps reduce operational costs in a practical way. Why Energy Management has Become Critical for Manufacturers Manufacturing operations depend heavily on electricity, gas, and compressed air. Machines, HVAC systems, lighting, and utilities all draw power throughout the day. Many plants still rely on periodic audits or manual readings. This approach delays insights and hides inefficiencies. Industry commentary published on TechNewsWorld notes that manufacturers who adopt continuous energy monitoring identify waste far earlier than those using traditional methods. This early visibility helps teams correct issues before they become expensive problems. Energy data also strengthens MES software solutions. When production and energy data exist together, decisions become more accurate and timely. What is a Smart Energy Management System? A smart energy management system is a digital platform that continuously monitors, analyses, and supports control of energy usage across a manufacturing facility. It collects data from machines, utilities, and infrastructure and converts that data into actionable insight. Unlike traditional energy tracking tools, Energy Management System software works in real time and supports automation. It does not rely on manual intervention or delayed reports. A typical smart system includes: This structure supports digital factory energy management, where energy becomes part of daily operational control. How a Smart Energy Management System Works A smart energy management system follows a structured process. First, sensors and meters collect energy data from machines, compressors, HVAC units, lighting systems, and utilities. This data flows continuously into the central platform. Next, the system analyses usage patterns. It compares current consumption with historical data, production schedules, and predefined benchmarks. This analysis highlights deviations that often go unnoticed. You then view these insights through dashboards. These dashboards show energy consumption by machine, line, or process. Alerts notify you when usage exceeds expected limits. Finally, the system supports action. Automated rules or manual interventions help adjust loads, schedule equipment, or investigate inefficiencies. This approach strengthens factory energy management without adding complexity for your teams. How Energy Management Systems Reduce Operational Costs Many manufacturers ask how energy management systems reduce operational costs in real terms. The impact appears across several areas. Reduced Peak Demand Charges Electricity tariffs often include penalties during peak demand hours. A smart system helps you identify high-load activities and shift them to off-peak periods. This alone can lower energy bills significantly. Lower Idle Energy Consumption Machines draw power even when idle. A smart energy management system identifies these periods and supports automated shutdowns or load reduction. This prevents unnecessary energy loss during non-productive hours. Improved Equipment Reliability Abnormal energy consumption often signals mechanical issues. Early detection allows maintenance teams to act before failures occur. This reduces repair costs and unplanned downtime. Better Energy Planning Accurate data improves forecasting and budgeting. You can plan production schedules with energy efficiency in mind. This helps balance output targets with cost control. Simplified Compliance and Reporting Energy audits and sustainability reporting require accurate data. Energy Management System software automates reporting, saving time and reducing manual effort. A 2024 analysis published by Wired reported that manufacturers using advanced energy analytics achieved energy cost reductions of up to 30% within the first year of deployment. The Role of MES Software Solutions in Energy Optimisation Energy insights become more valuable when linked with production data. MES software solutions enable this connection. When energy management integrates with MES – This unified view helps you make decisions that improve both productivity and cost control. It also supports continuous improvement initiatives across the factory. Smart Energy Management in a Digital Factory Environment In a digital factory, systems do not operate in isolation. Energy management works alongside automation, machine monitoring, and analytics platforms. Digital factory energy management focuses on continuous visibility, data-driven decisions, and automated optimisation. This approach allows manufacturers to treat energy as a variable they can control rather than a fixed expense. Prescient Technologies supports this approach by delivering digital factory platforms that connect energy data with manufacturing operations. These platforms help teams gain better visibility, control, and operational insight. Common Challenges without Smart Energy Management Without a smart system, manufacturers often face: These challenges grow as factories scale or adopt advanced automation. A smart system addresses these issues by making energy data accessible and actionable. Who Should Consider a Smart Energy Management System? A smart energy management system suits organisations that operate energy-intensive production lines or manage multiple facilities. It also fits companies planning digital transformation or already using MES software solutions. Manufacturing professionals, CTOs, R&D teams, and IT leaders benefit from improved energy visibility and control. This visibility supports strategic planning as well as day-to-day operations. Key Takeaways Take the Next Step If you want better control over energy costs without disrupting production, smart energy management is a practical step forward. Connecting energy data with factory operations helps you identify inefficiencies and act quickly. Explore how Prescient Technologies’ digital factory solutions support smart energy monitoring and optimisation. Their platforms help manufacturing teams gain actionable insight and improve operational performance. Connect with the Prescient team to understand how smart energy intelligence can support your factory goals. Your PLM system should evolve with your business not trap it in place. Yet countless manufacturers discover this truth too late, when a seemingly simple software upgrade becomes a six-month ordeal requiring extensive code rewrites and threatening business continuity. The difference between configurable and customized PLM isn’t just technical semantics. It’s the difference between a system that grows with you and one that eventually holds you hostage. The Upgrade Lock-in
Read More1. What is IIoT?
The Industrial Internet of Things (IIoT) refers to the integration of industrial processes, machinery, and devices with Internet connectivity, allowing for real-time data collection, analysis, and communication. It enables industries to enhance operational efficiency, optimize processes, and make data-driven decisions.
2. How can IIoT solutions benefit my business?
IIoT solutions offer numerous benefits to businesses, including: 1) Improved operational efficiency and productivity 2) Enhanced asset utilization and maintenance 3) Real-time monitoring and analytics for informed decision-making 4) Increased visibility and transparency across the supply chain 5) Energy optimization and cost savings 6) Enhanced quality control and traceability 7) Proactive maintenance and reduced downtime
3. What IIoT solutions does Prescient Technologies provide?
1) Prescient Technologies offers a comprehensive suite of IIoT solutions, including: 2) Management dashboard for real-time data visualization and analytics 3) Material Traceability for end-to-end visibility and tracking of materials 4) OEE Monitoring for equipment performance optimization 5) Energy management for efficient energy consumption 6) Asset Management for remote monitoring and asset maintenance
4. Can I customize IIoT solutions to fit my specific business needs?
Yes, Prescient Technologies understands that businesses have unique requirements. Our IIoT solutions are customizable and scalable to adapt to your specific business needs, ensuring a tailored fit and maximum value.
5. How do I integrate IIoT solutions with my existing systems?
Prescient Technologies specializes in seamless integration with existing systems and infrastructure. Our expert team will work closely with you to ensure smooth integration, minimal disruption, and maximum compatibility.
6. Are IIoT solutions secure?
Prescient Technologies prioritizes data and system security. Our IIoT solutions implement robust security measures to protect against cyber threats and ensure compliance with industry standards and regulations.
7. How long does it take to implement IIoT solutions?
The implementation time for IIoT solutions can vary based on the complexity of your requirements. Prescient Technologies follows a streamlined implementation process and strives to minimize downtime during transition. The timeline will be discussed and planned during the initial consultation.
8. Do you provide training and support for IIoT solutions?
Yes, Prescient Technologies offers comprehensive training and onboarding to ensure that your team is equipped to utilize the IIoT solutions effectively. For more details contact us.
9. Can you provide examples of successful IIoT implementations?
Absolutely! Prescient Technologies has a track record of successful IIoT implementations across various industries. We have case studies and testimonials from satisfied clients that demonstrate the positive impact our solutions have had on their businesses.
10. How can I get started with Prescient Technologies' IIoT solutions?
To get started, simply reach out to us through contact@pre-scient.com. We will schedule a consultation to understand your specific requirements and propose the most suitable IIoT solutions for your business. Our team will guide you through the entire process, from solution design to implementation and ongoing support.